AWS DynamoDB
Source
Polytomic offers the following methods for connecting to DynamoDB:
- AWS Access Key ID and Secret
- AWS IAM role
Each method is covered in its respective section below.
Connecting with an AWS Access Key ID and Secret
- In Polytomic, go to Connections → Add Connection → DynamoDB.
- For Authentication method, select Access Key and Secret:
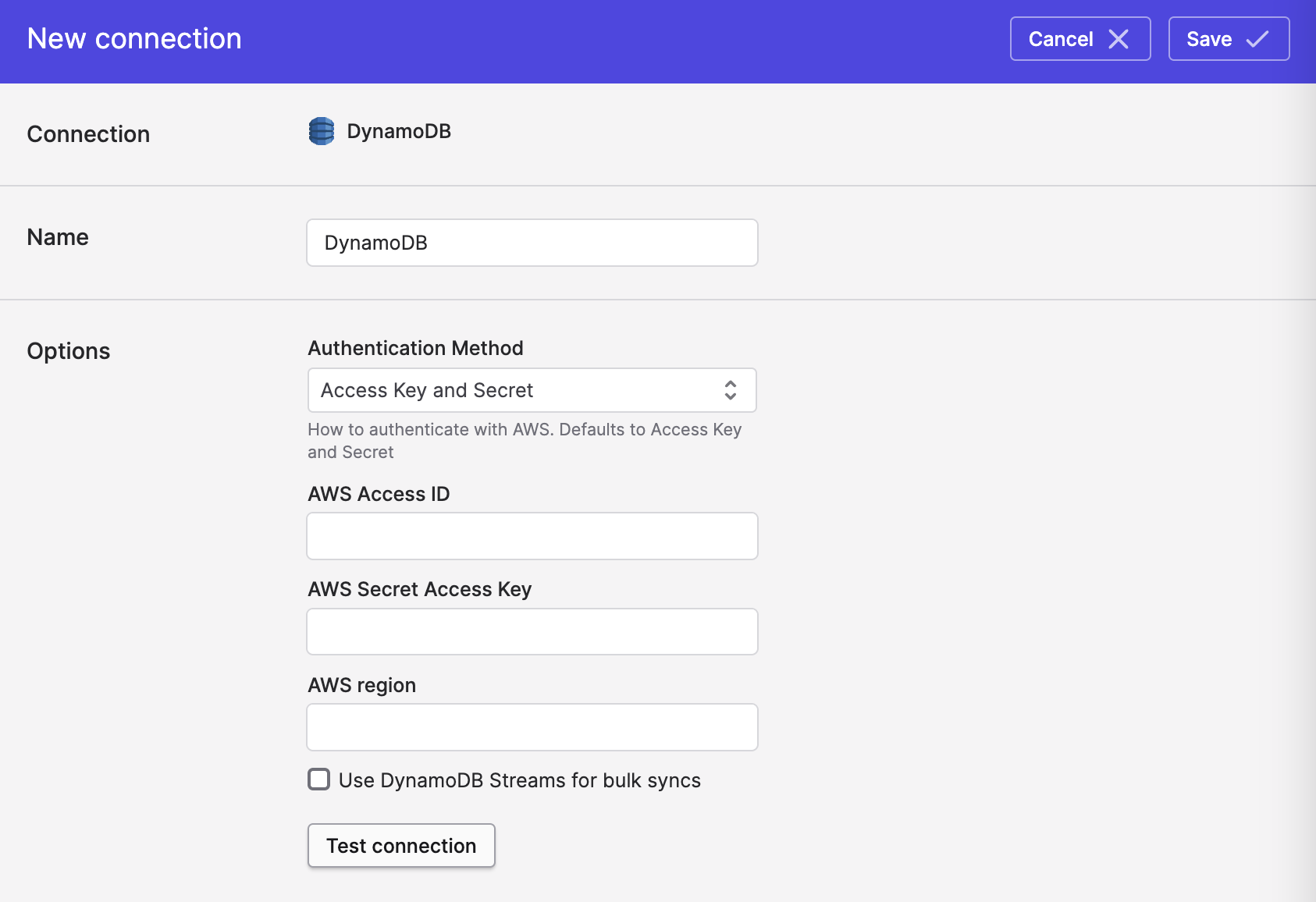
- Enter the following information:
- AWS Access ID
- AWS Secret Access Key
- AWS region (e.g.
us-west-1)
- Optional: if you are syncing from DynamoDB, it is recommended that you enable the Use DynamoDB Streams for bulk syncs option. See the Syncing from DynamoDB section below for details.
- Click Save.
Connecting with an AWS IAM Role
- In Polytomic, go to Connections → Add Connection → DynamoDB.
- For Authentication method, select IAM role:
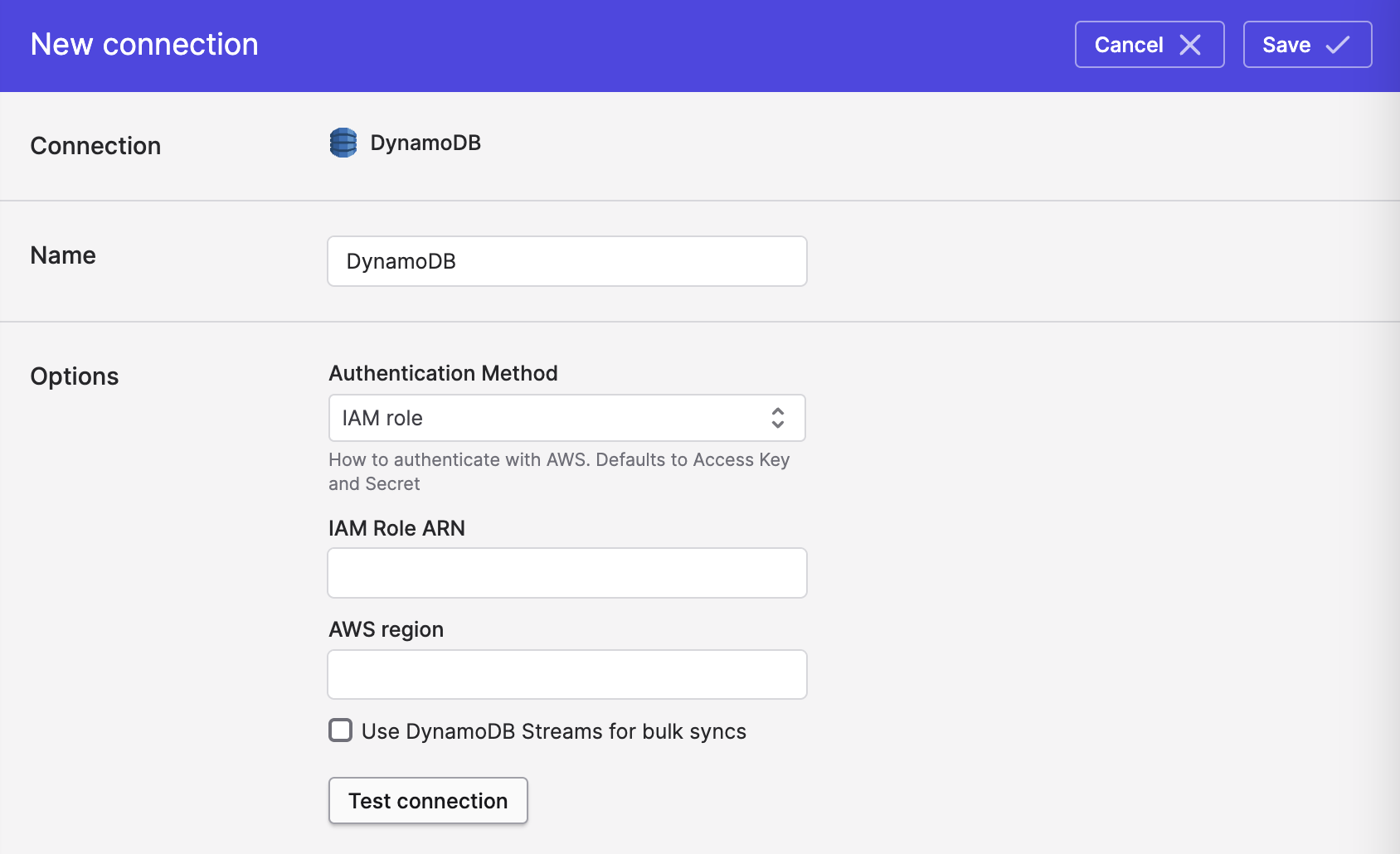
- Enter values for the following fields:
- IAM Role ARN.
- AWS region (e.g.
us-west-1).
- Click Save.
IAM Permissions
Polytomic uses the following IAM Actions when reading from DynamoDB:
dynamodb:BatchGetItemdynamodb:Describe*dynamodb:List*dynamodb:GetItemdynamodb:Querydynamodb:Scandynamodb:PartiQLSelect
AWS's documentation lists some example policies here.
Additional permissions when using DynamoDB Streams
When the "Use DynamoDB Streams for bulk syncs" checkbox is set, a bulk sync will enable a DynamoDB Stream for each table being synced and use that to read changes.
Polytomic will configure a DynamoDB Stream for each table selected for syncing. A DynamoDB table may only have a single Stream associated with it. If a DynamoDB Stream exists for a table and and the view does not include new row images (e.g.,
StreamViewTypeofKEYS_ONLYorOLD_IMAGE), it will be replaced.
The following IAM action must be allowed for tables; this allows Polytomic to manage the DynamoDB stream:
dynamodb:UpdateTable
The following IAM actions must be allowed for on streams, in order to read the changes:
dynamodb:GetRecordsdynamodb:GetShardIteratordynamodb:DescribeStreamdynamodb:ListStreams
These need to be allowed for the stream resource, not the table. If you're specifying resources the identifiers follow the pattern "arn:aws:dynamodb:us-west-2:123456789012:table/tableName/stream/*", where tableName is the name of individual DynamoDB tables to allow. See the AWS documentation for more information.
Role Assumption
In addition to operating permissions, the role must be assumable by Polytomic. A trust policy that allows Polytomic to assume the role will look like the following:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::568237466542:root"
},
"Action": "sts:AssumeRole"
}
]
}
Restricting the trust policy
Using an external identifier
When you click Save Polytomic will generate an External ID. This can be used to further limit who is able to assume the provided role. If you return to the Polytomic DynamoDB connection, you'll see the External ID below the Role ARN.
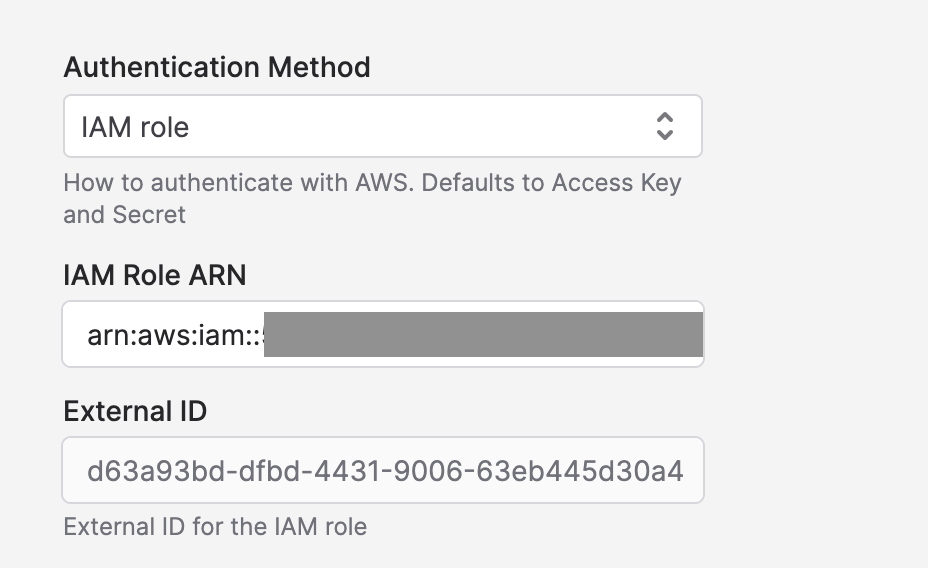
Generated External ID displayed on the DyanmoDB connection after saving
A trust policy that verifies the External ID before allowing Polytomic to connect will look like the following (substitute the sts:ExternalId value with that from the field above):
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::568237466542:root"
},
"Action": "sts:AssumeRole",
"Condition": {
"StringEquals": {
"sts:ExternalId": "0000"
}
}
}
]
}
Restricting assumption to a role
You can further restrict who can assume your role by specifying the following role from Polytomic's account as the principal:
arn:aws:iam::568237466542:role/convox/prod-polytomic-ServiceRole-1ELGH39L0GCHT
Syncing from DynamoDB
Warehouse and cloud storage destinations
Use Bulk Syncs when syncing from DynamoDB to your data warehouses, databases, and cloud storage buckets.
We recommend enabling CDC (change data capture) streaming from DynamoDB's Streams, as this avoids full table scans and instead reads updates from DynamoDB's changestream. You can enable this by ticking the Use DynamoDB Streams for bulk syncs box on your DynamoDB connection:
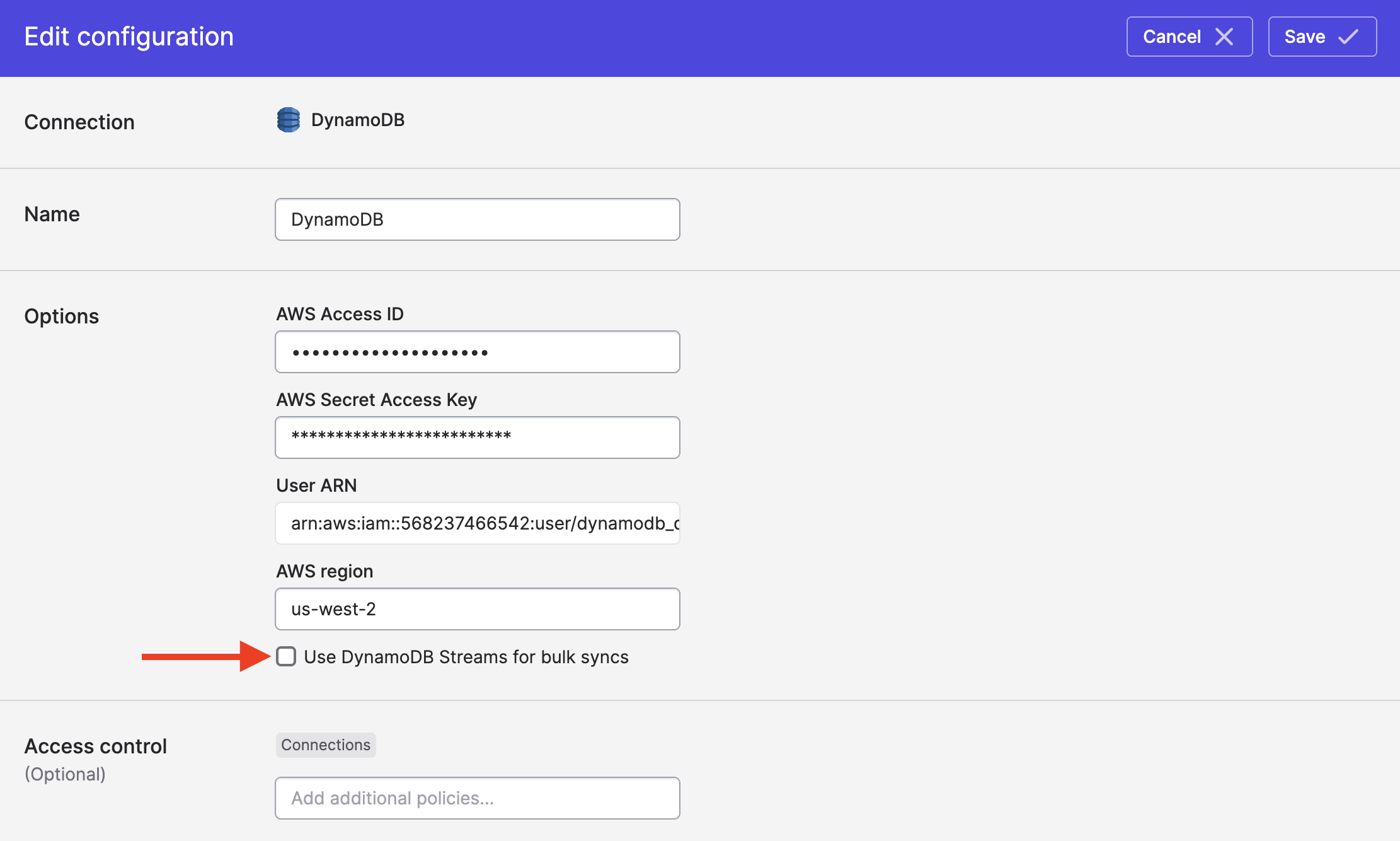
To have Polytomic automatically manage DynamoDB Stream settings for you, be sure to tick the subsequent box that says Let Polytomic manage DynamoDB Stream settings:
Leaving the second box unticked means that you will have to enable the DynamoDB Stream yourself for any table you want to sync from with CDC. Doing this yourself removes the need for granting Polytomic the dynamodb:UpdateTable permission.
SaaS application destinations
Use Model Syncs when syncing DynamoDB to SaaS applications like Salesforce, HubSpot, Zendesk, and so on.
Considerations when using Model Syncs from DynamoDB
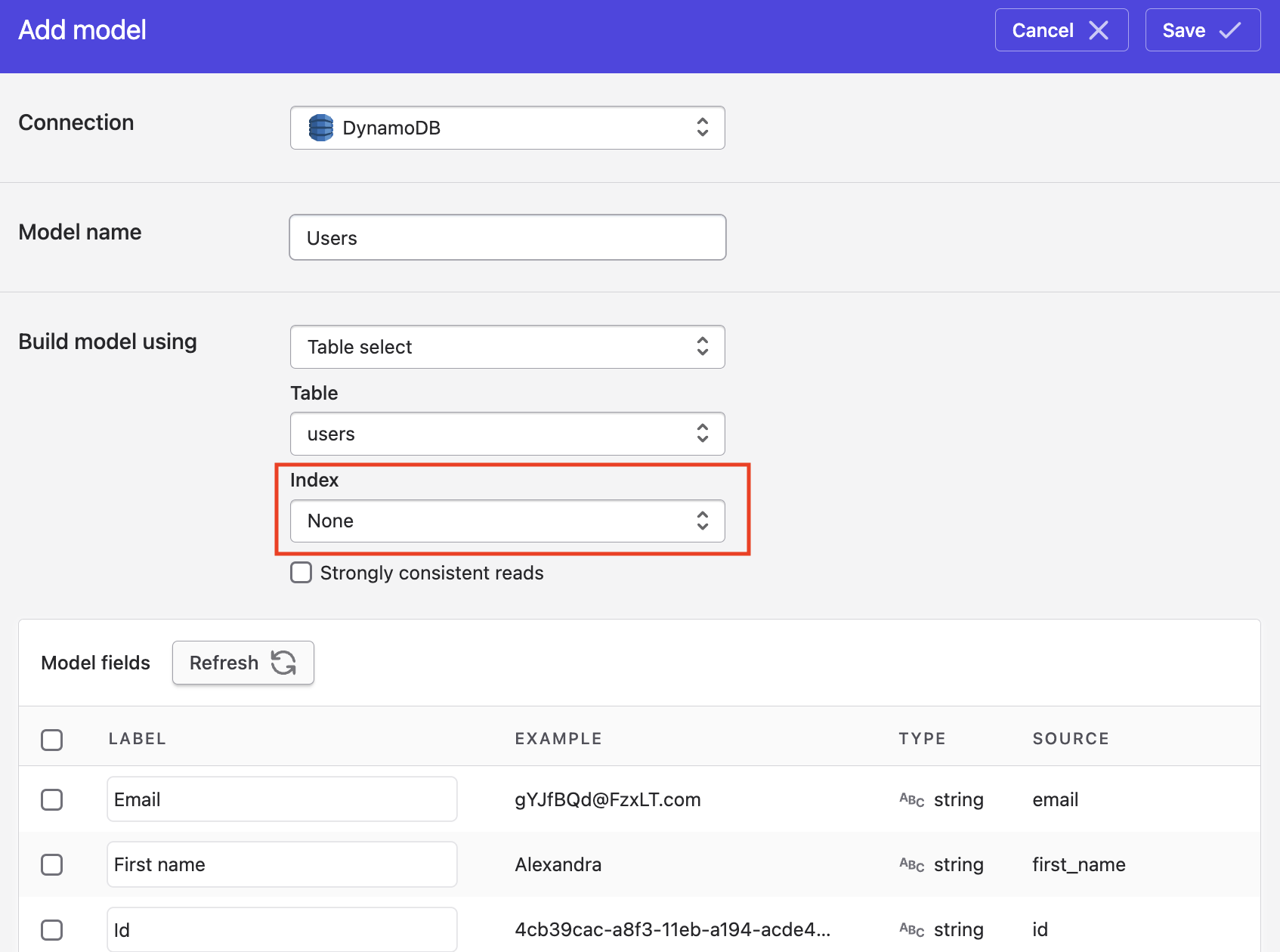
Secondary index
When building a Polytomic model on a DynamoDB table with a secondary index, you have the option of pointing Polytomic to your secondary index using the Index dropdown. Doing so will avoid full table scans:
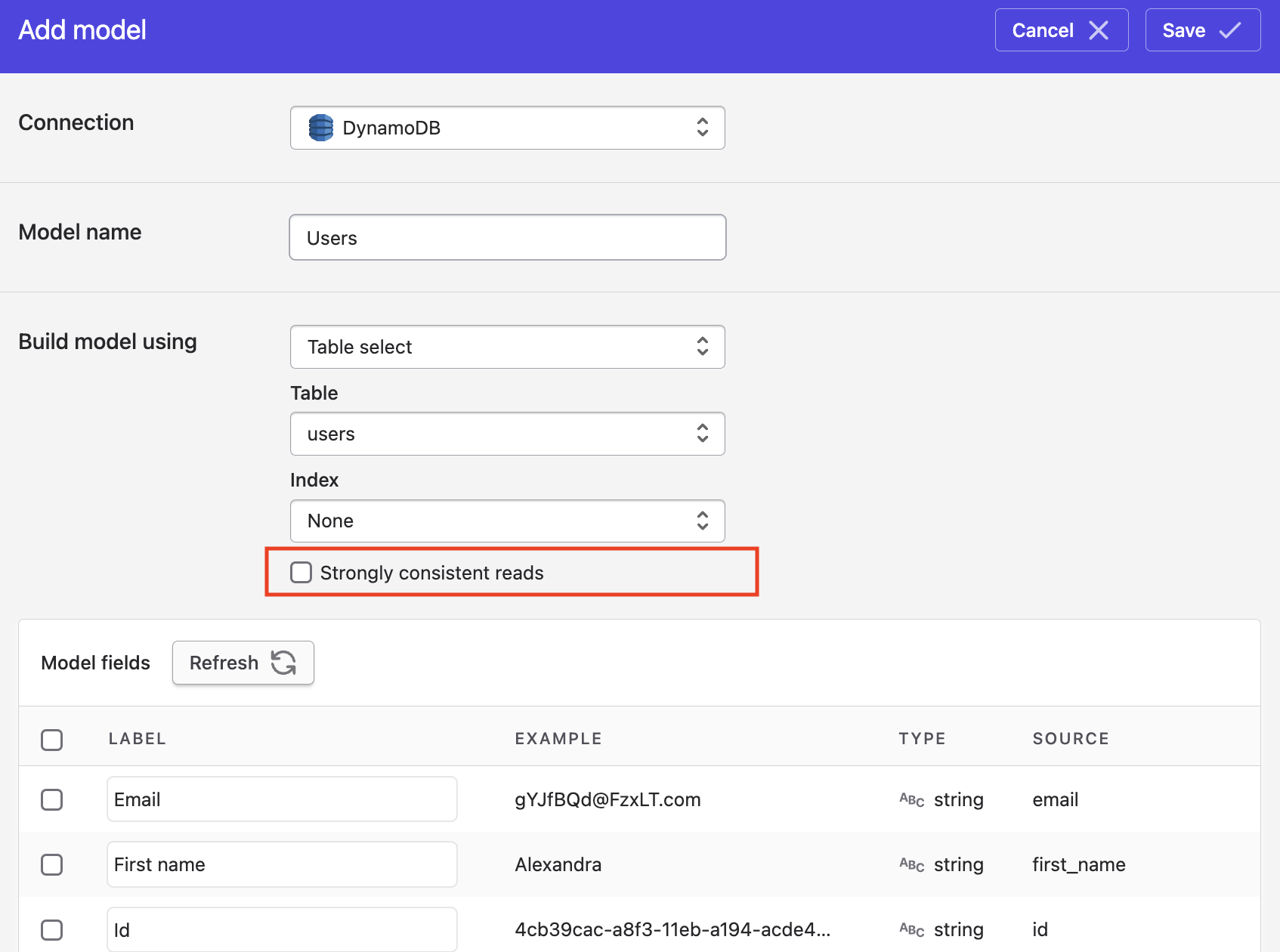
Strongly consistent reads
By default, DynamoDB's read model is an eventually consistent one. That is, the response for a read operation may not include the result of a recently-completed write operation. This keep read throughput high.
You can override this within Polytomic. To have Polytomic carry out strongly consistent reads, tick the Strongly consistent reads box in your Polytomic model editor. The tradeoff is that your reads will take a bit longer:
Updated 5 months ago