Custom roles
Introduction
Polytomic's permissions engine is a true RBAC (role-based access control) system that allows you to define your own user roles with custom security policies that dictate what set of operations are allowed for those roles. You can, for example, define different roles that:
- Are not allowed to sync to Snowflake.
- Are only allowed to sync to Salesforce.
- Are not allowed to create or edit connections.
The above are just a few examples. The set of possibilities is large as the system is exceptionally flexible.
Paid add-on
The ability to define custom roles and policies is a paid add-on. Contact [email protected] to request access.
Let's go over the system's components.
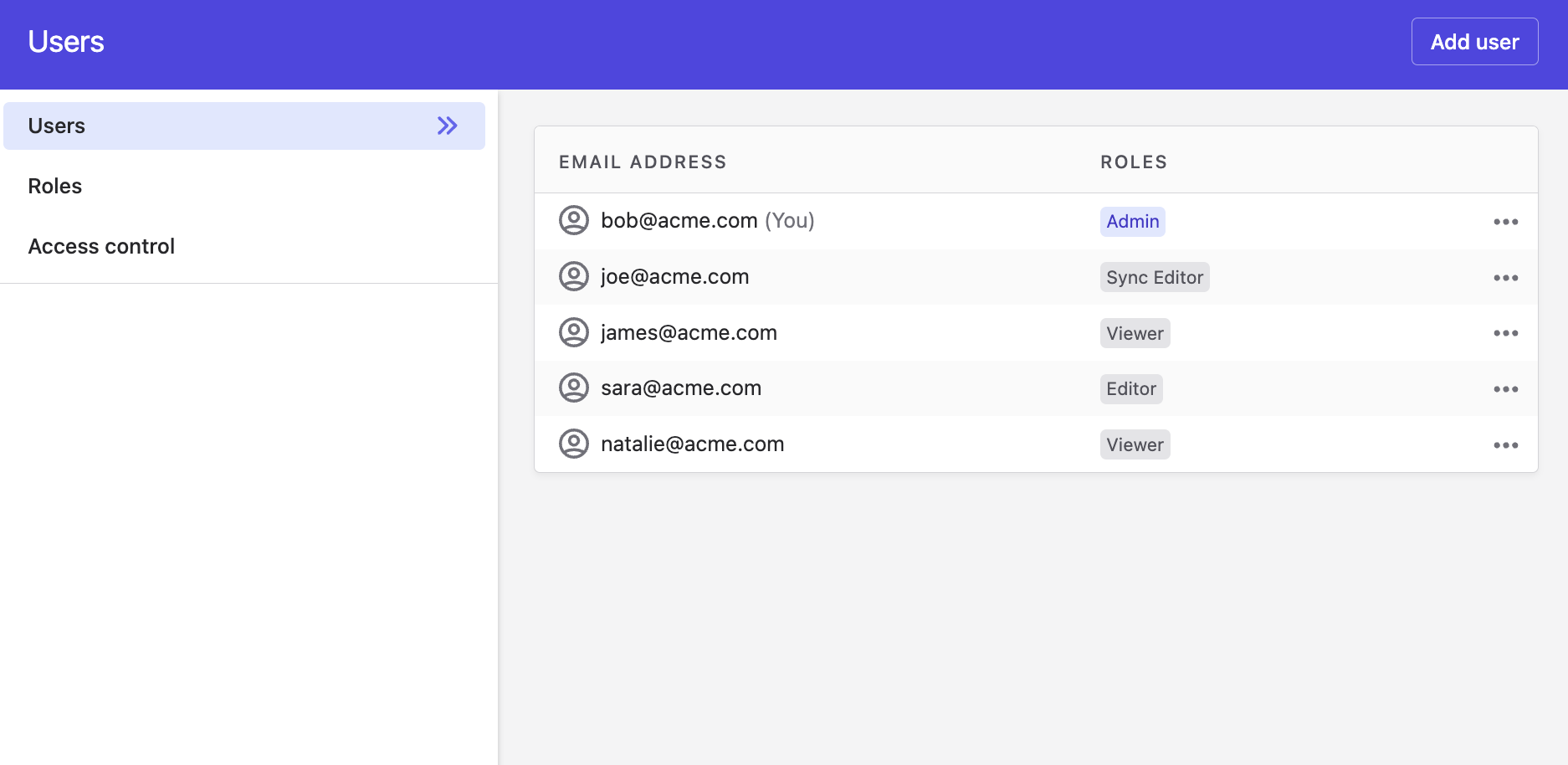
Users
These are individuals with access to Polytomic, identified by their email addresses.
Roles
Roles in Polytomic are labels (e.g. Admin or Viewer). Users can have one or more roles and Polytomic comes with default roles.
Note that, as roles are merely text labels, they enforce nothing on their own. To actually enforce permissions they need to be coupled to policies which are covered next.
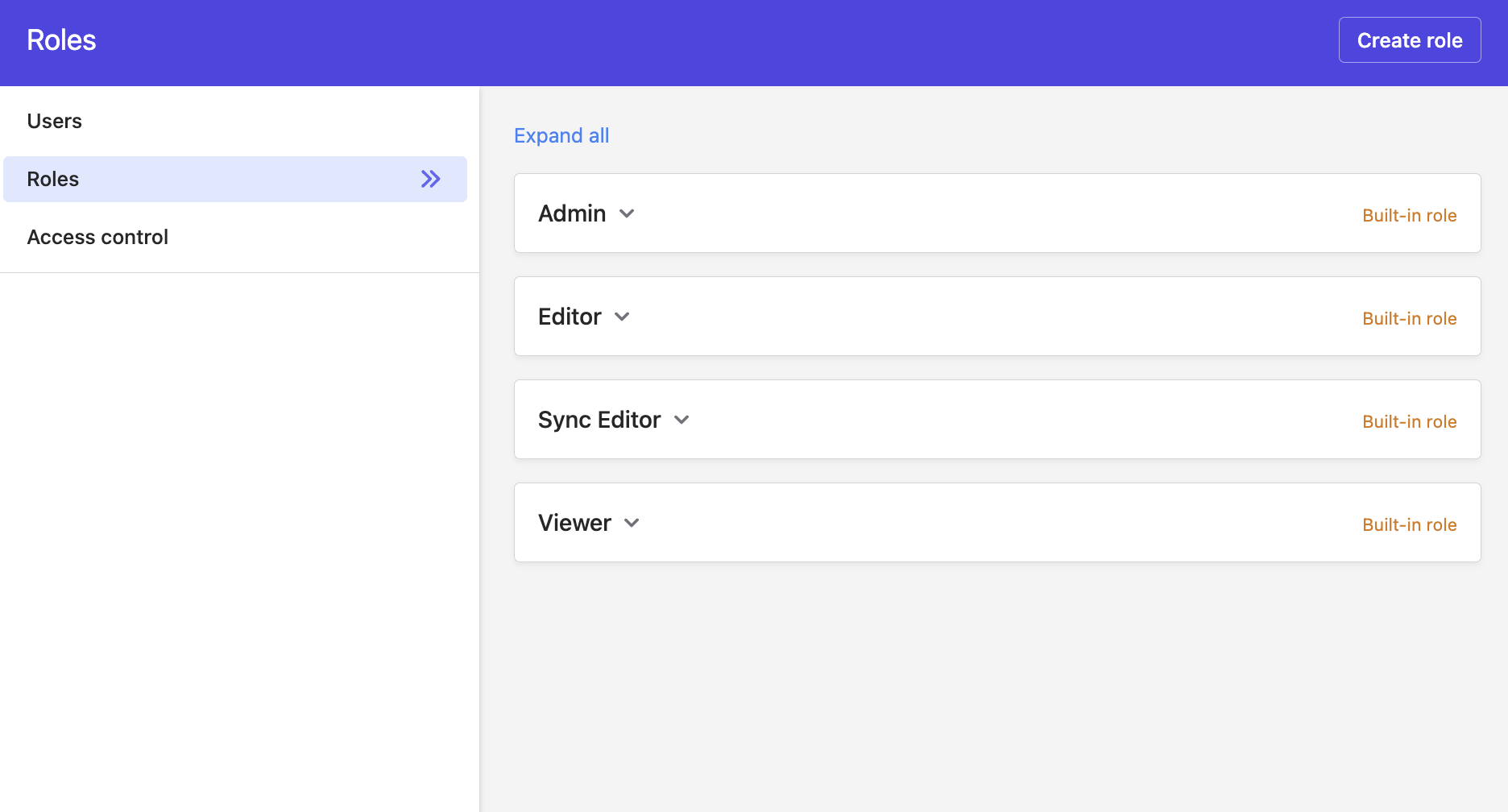
Policies
A policy is what dictates access control, i.e. what capabilities are enabled for what role. This is the deciding component in the Polytomic permissions engine.
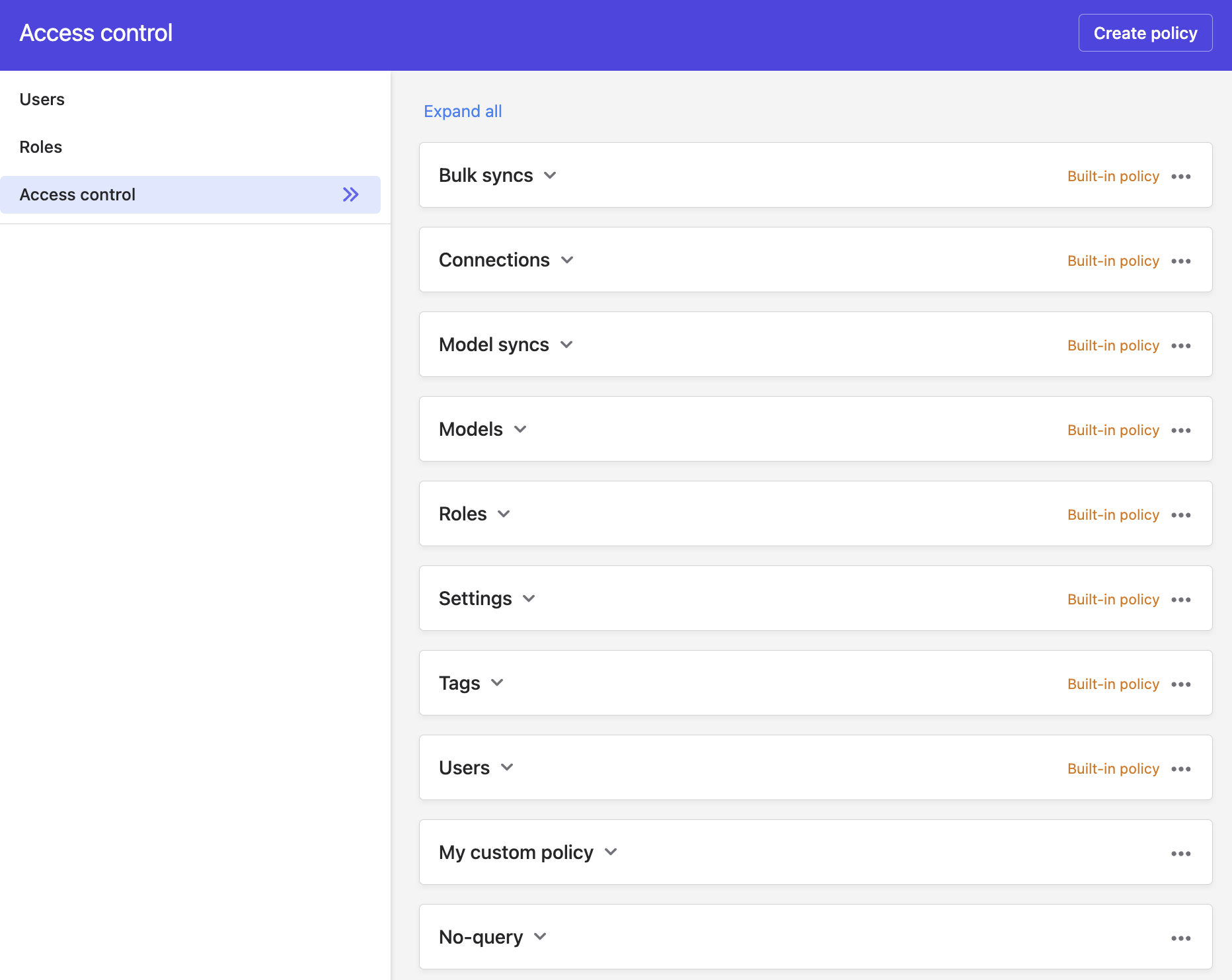
Policy actions
A policy consists of actions and each action can be enabled for one or more roles.
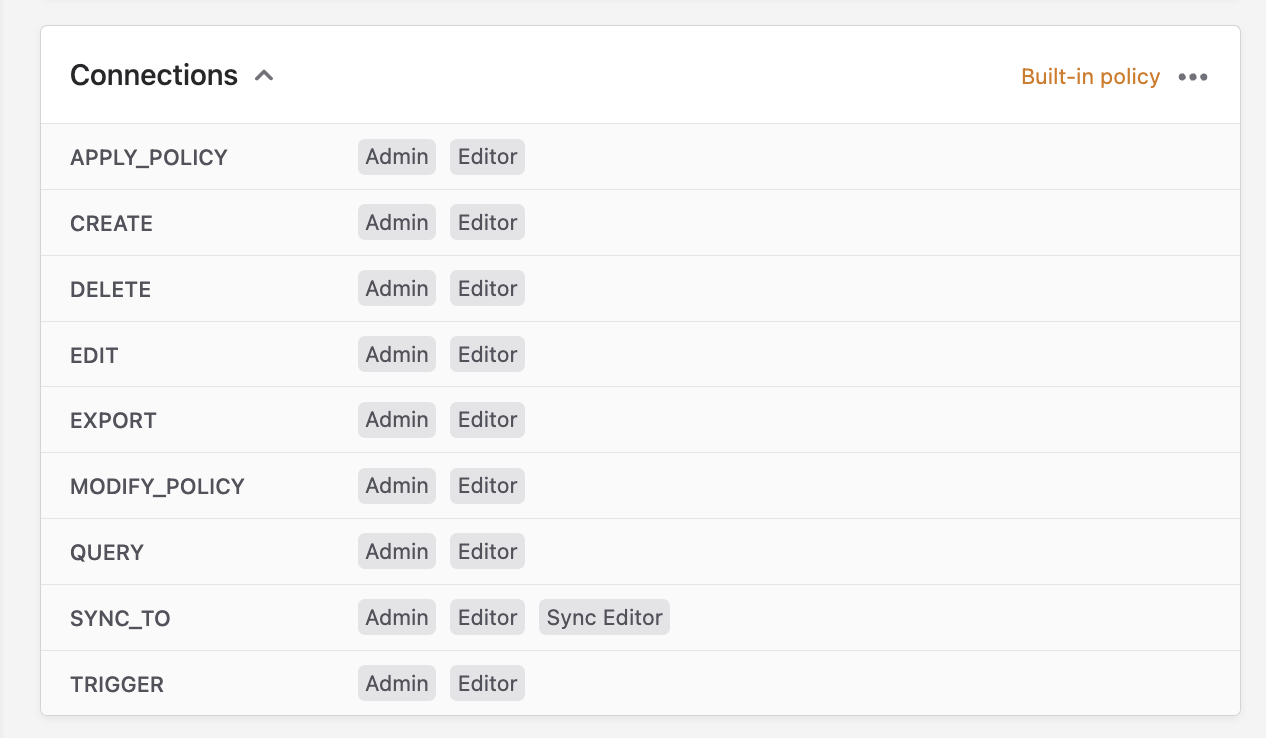
To enforce a policy, you must attach it to an object in Polytomic (for example: a model, sync, or connection). That object will then only allow each of the policy's actions for the roles attached to them.
Each policy in Polytomic comes with the same list of actions listed in the screenshot above. We'll explain each action by explaining what the above policy (a built-in one attached to all connections in Polytomic) means:
- apply_policy: only the Admin and Editor roles can attach this policy to objects in Polytomic.
- create: only the Admin and Editor roles can create connections.
- delete: only the Admin and Editor roles can delete connections.
- edit: only the Admin and Editor roles can edit connections.
- export: only the Admin and Editor roles can export data from connections.
- modify_policy: only the Admin and Editor roles can modify this policy.
- query: only the Admin and Editor roles can run queries on connections (this includes model-building, as models are ultimately queries).
- sync_to: only the Admin, Editor, and Sync Editor roles can sync to connections.
- trigger: only the Admin and Editor roles can trigger syncs.
You must attach policies to an object in order for them to be enforced. The above system policy is enforced only because Polytomic attaches it to each connection (as it is a system policy).
Editing built-in policies
Polytomic comes with a set of built-in policies that automatically attach themselves to all objects of a specific type (e.g. models, connections, syncs, etc). Editing a built-in policy affects all instances of its object (for example, editing the default Connections policy will affect all Polytomic connections).
Nullifying built-in policies
You can nullify built-in policies by removing all roles from their actions.
Creating custom policies
The Admin role can create any number of policies and choose what roles have access to the policies' actions. These custom policies can then be attached to any object in Polytomic and that object will then obey its attached policies.
Let's walk through two examples in the subsequent sections.
Updated 10 months ago