Using AWS IAM roles to access S3 buckets
Instructions for configuring Polytomic using AWS IAM role assumption.
Polytomic supports using AWS IAM roles to access S3 buckets for several connection types.
- AWS S3 for providing read and write access to a bucket.
- Databricks for accessing an S3 bucket used to stage data during syncs.
- Redshift Serverless for accessing an S3 bucket used to stage data during syncs, and for reading data using
UNLOADoperations.
This page describes common configuration settings for these connections.
S3 Permissions
Polytomic requires the following permissions when writing to S3 buckets, either directly or as a staging area for other connections.
s3:GetObjects3:ListBuckets3:PutObjects3:DeleteObjects3:GetBucketLocation
These permissions should be granted for the bucket and the wildcard (*) object in the bucket.
For example, a valid IAM policy for a bucket named syncoutput would be as follows.
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "PolytomicBucket",
"Effect": "Allow",
"Action": [
"s3:GetObject",
"s3:ListBucket",
"s3:PutObject",
"s3:DeleteObject",
"s3:GetBucketLocation"
],
"Resource": [
"arn:aws:s3:::syncoutput/*",
"arn:aws:s3:::syncoutput"
]
}
]
}
Role Assumption
In addition to operating permissions, the role must be assumable by Polytomic. A trust policy that allows Polytomic to assume the role will look like the following:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::568237466542:root"
},
"Action": "sts:AssumeRole"
}
]
}
Some integrations such as Redshift Serverless require additional trust clauses; consult the integration documentation for details.
Some integrations support setting additional tags when the role is assume. If you are configuring the connection with additional tags, please make sure to include the sts:TagSession permission in your trust policy:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::568237466542:root"
},
"Action": [
"sts:AssumeRole",
"sts:TagSession"
]
}
]
}
Specifying an IAM role for your connection
- When creating an S3, Databricks, or Redshift connection, choose IAM role for the Authentication method.
- Enter the IAM Role ARN Polytomic will assume when connecting to the bucket.
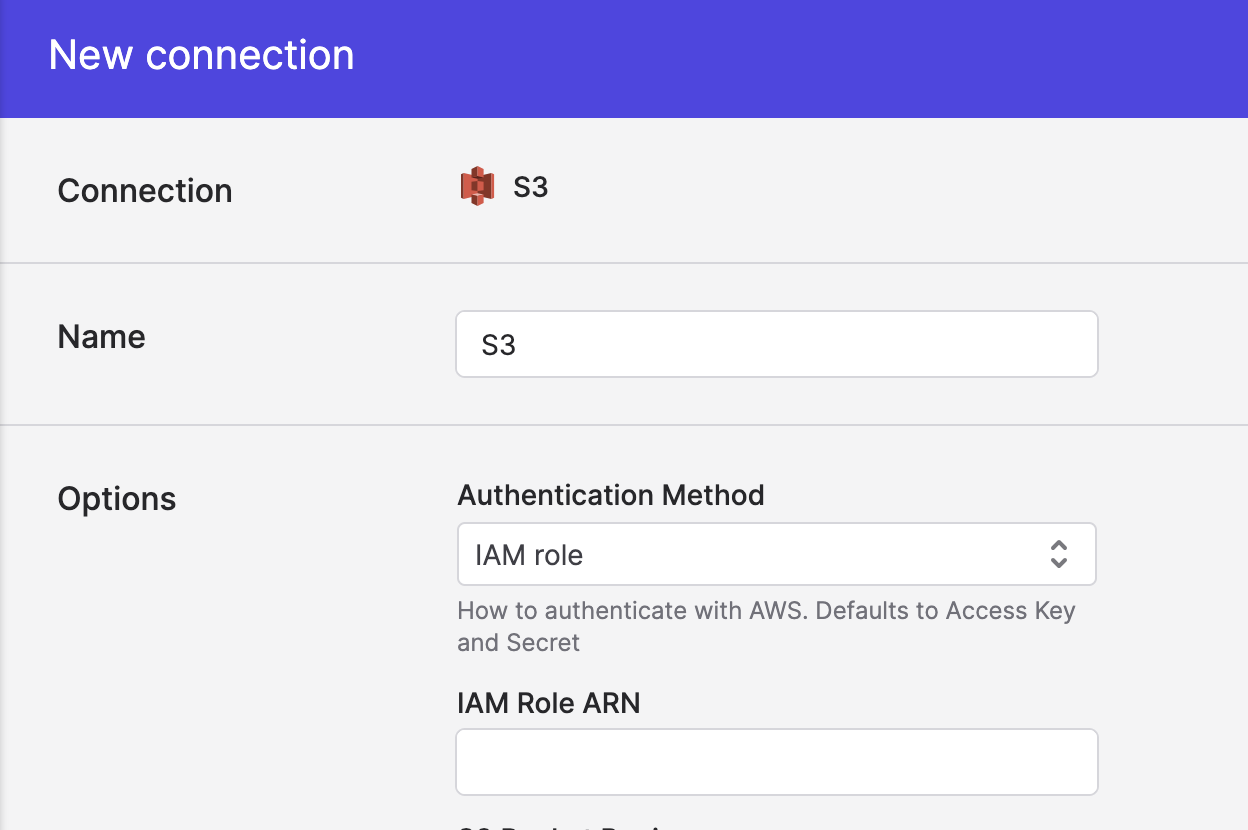
Creating a new S3 connection with IAM role selected as the authentication method.
- Click Save.
Restricting the trust policy
Using an external identifier
When you click Save Polytomic will generate an External ID, which can be used to further limit who is able to assume the provided role. If you return to the connection, you'll see the External ID below the Role ARN.
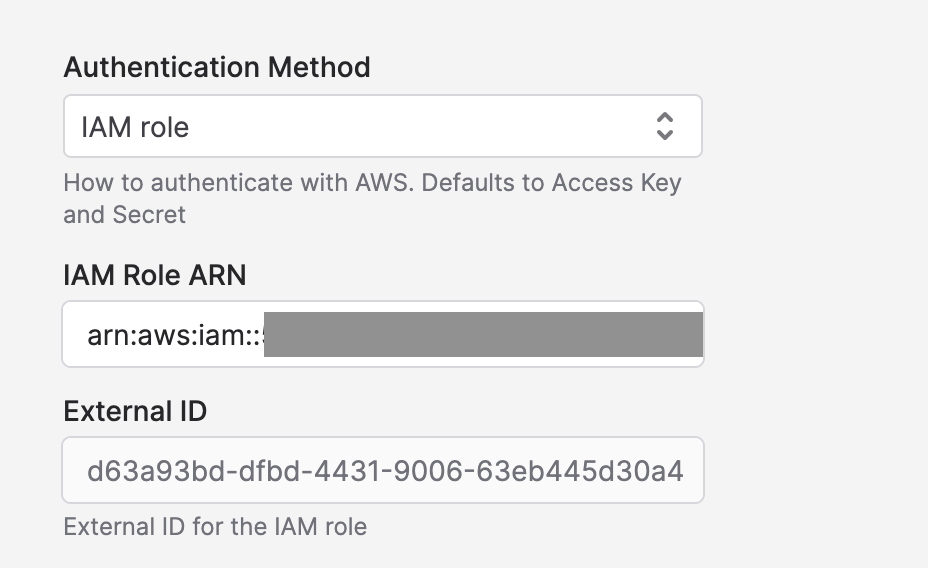
S3 connection details after saving, displaying the generated External ID.
A trust policy that verifies the External ID before allowing Polytomic to connect will look like the following:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::568237466542:root"
},
"Action": "sts:AssumeRole",
"Condition": {
"StringEquals": {
"sts:ExternalId": "0000"
}
}
}
]
}
Note that the value for sts:ExternalId is specific to your Polytomic connection.
Restricting assumption to a role
You can further restrict who can assume your role by specifying the following role from Polytomic's account as the principal:
arn:aws:iam::568237466542:role/convox/prod-polytomic-ServiceRole-1ELGH39L0GCHT
Updated about 2 months ago