Example: restrict model-editing
What if you want to restrict the ability to create, edit, and delete Polytomic models to particular roles?
In this case there is no need to create a new policy (although you could if you wanted to). You can instead edit the built-in Models policy:
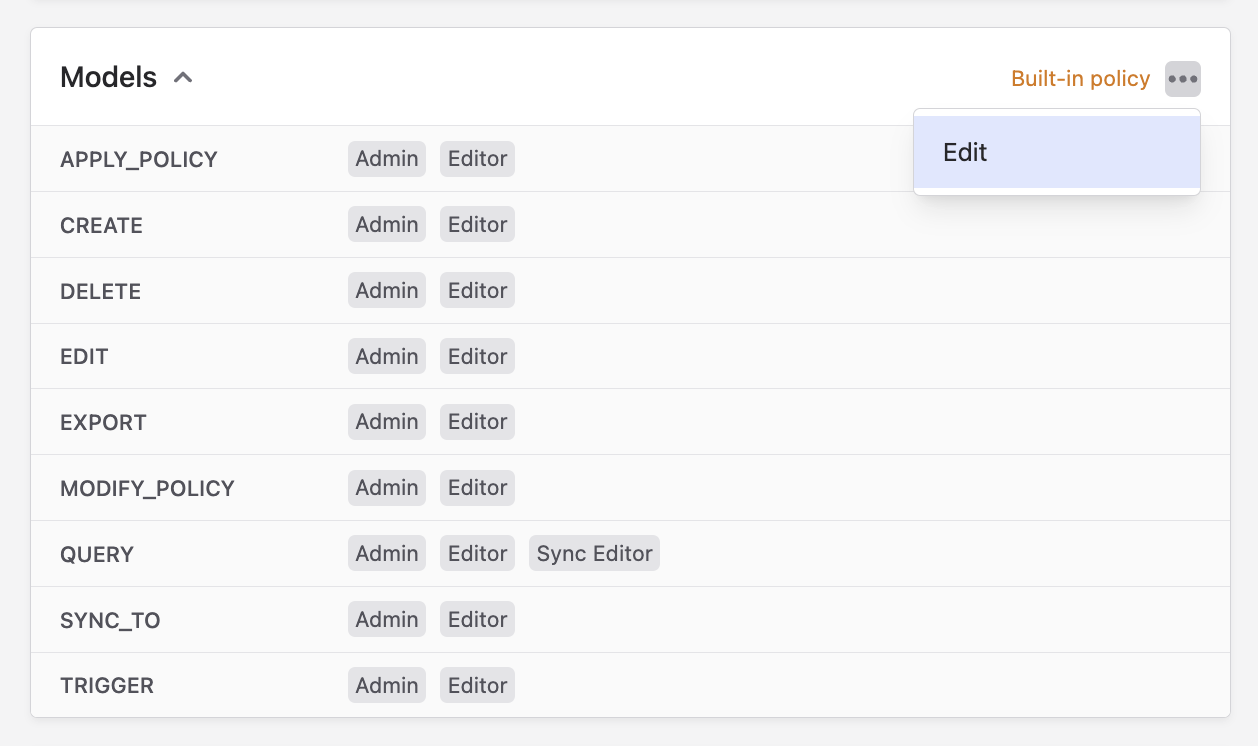
- Click the three dots in the top-right to edit the policy:
-
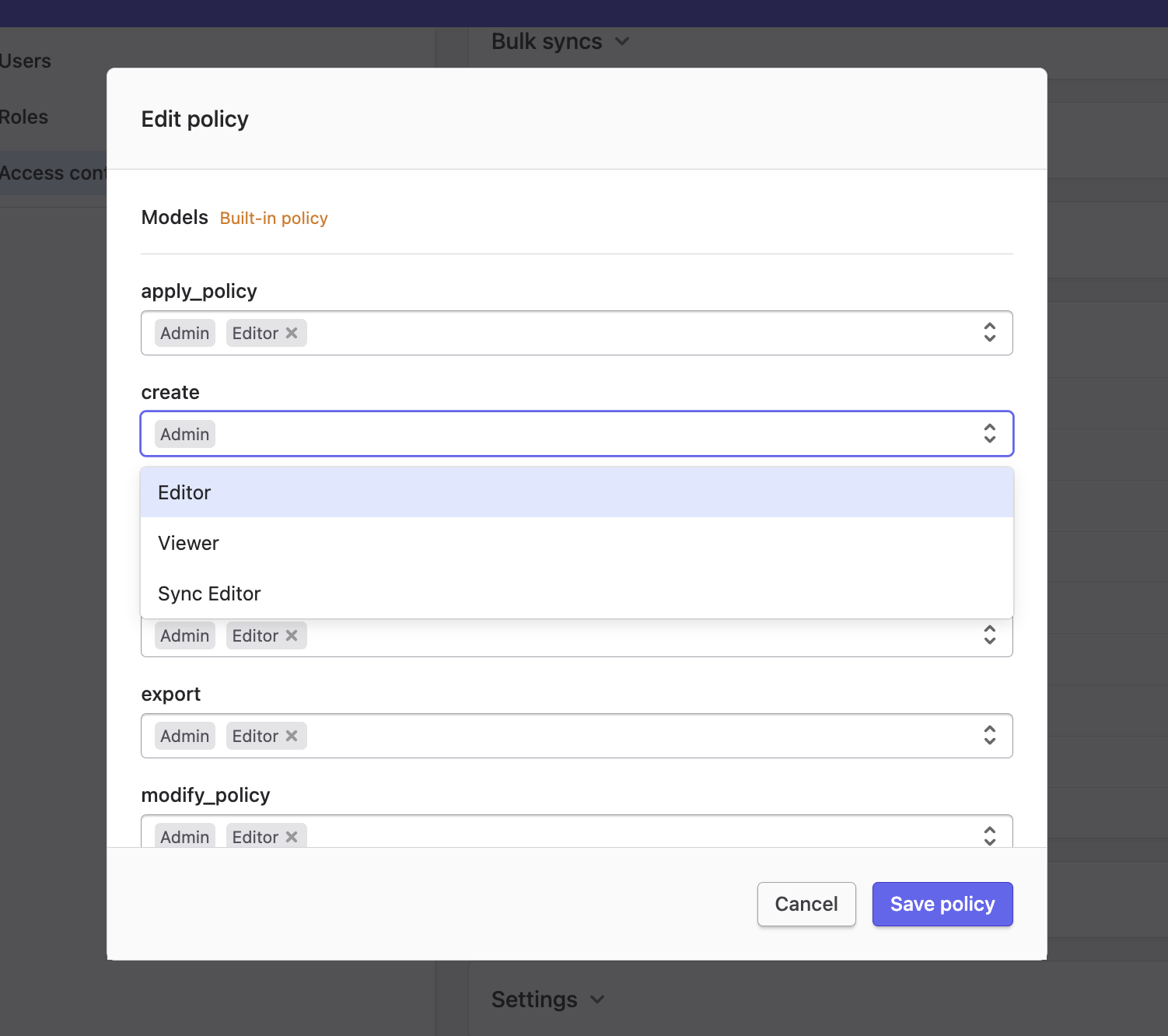
Pick the authorised roles for the create, delete, and edit actions.
-
Save your policy.
This is a built-in policy that is automatically attached (thus enforced) to all models in Polytomic.
Inapplicable actions
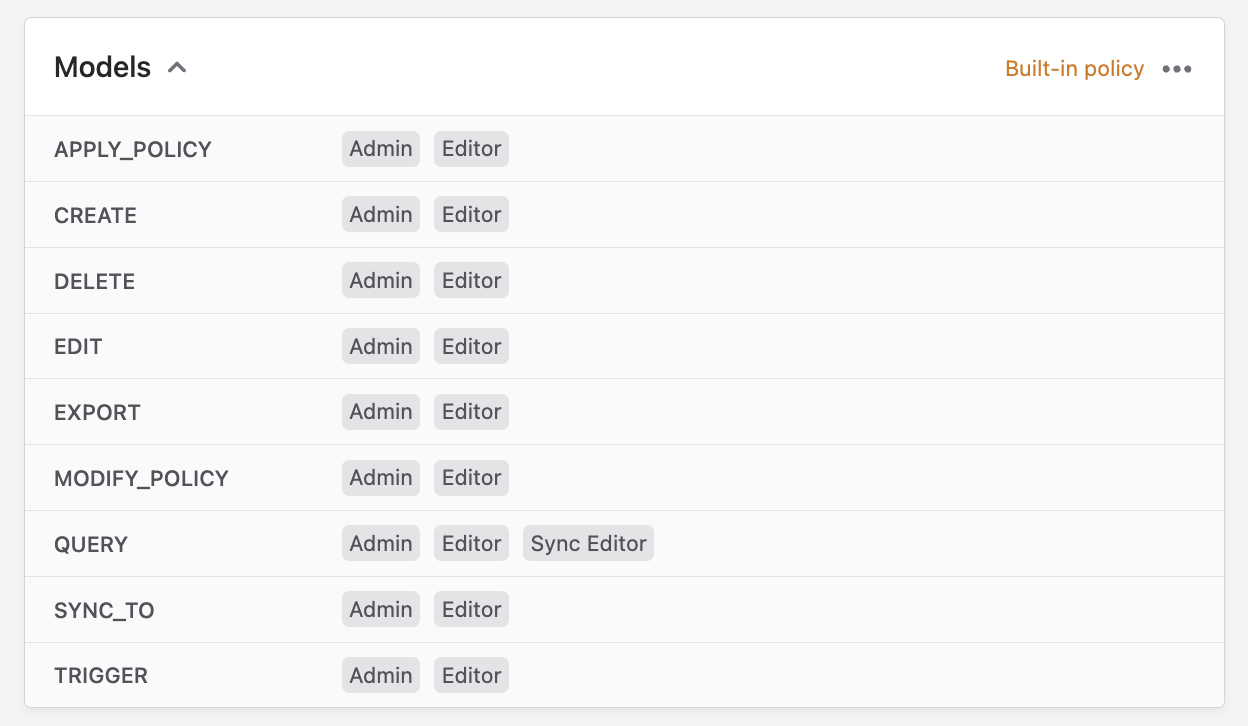
You will notice that not every single action on a policy will apply to all objects. For example, the default policy above contains actions like sync_to and trigger:

It does not make sense to 'sync to' or 'trigger' a model. In situations where a policy action is inapplicable to an object, it and its attributes are ignored by that object. In the case of models, one may as well leave the sync_to and trigger actions blank.
Updated almost 3 years ago