AWS Athena
Source and destination
- In Polytomic, go to Connections → Add Connection → AWS Athena:
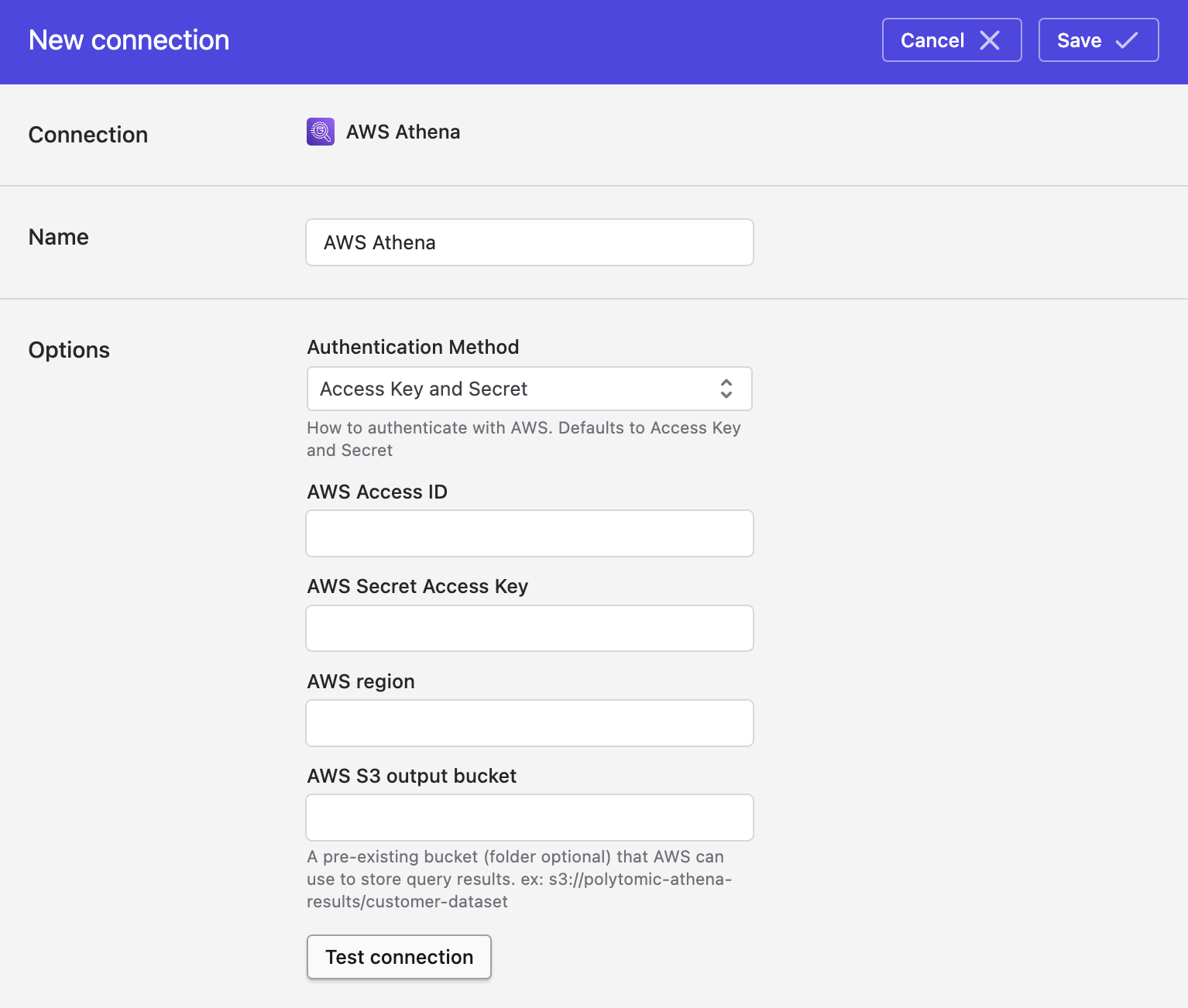
- If authenticating with an AWS Access Key and Secret, fill in the following fields:
- AWS Access ID
- AWS Secret Access Key
Alternatively, if authenticating with an IAM role, switch the Authentication Method dropdown to IAM role and enter your IAM role ARN:
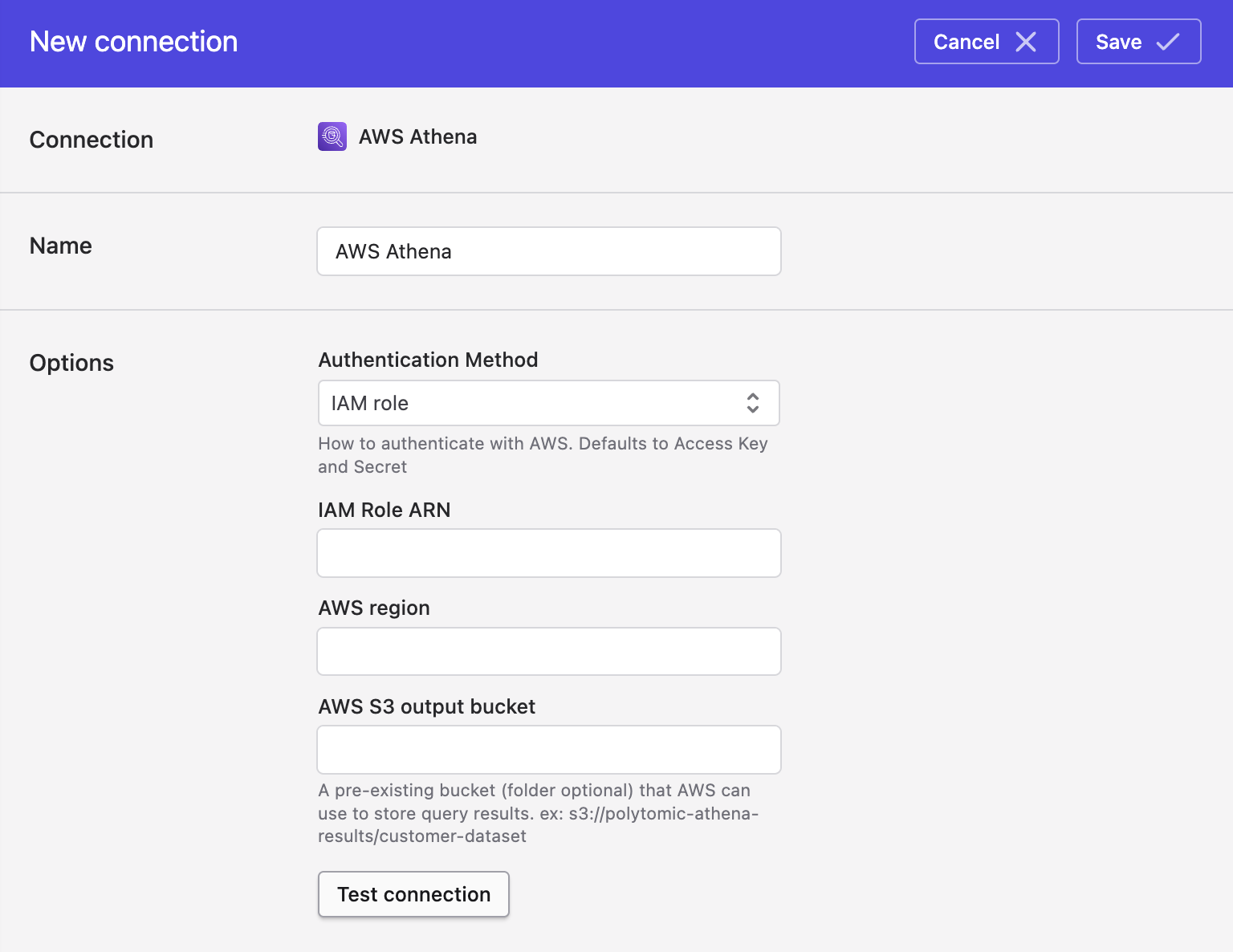
- Fill in the following fields:
- AWS region (e.g.
us-west-1) - AWS S3 output bucket
- Click Save.
IAM Permissions
Polytomic uses the following IAM Actions when introspecting Athena. Most users will grant these to the catalogs, databases, and tables they wish to use with Polytomic.
athena:GetNamedQueryathena:GetDataCatalogathena:GetPreparedStatementathena:GetQueryExecutionathena:GetQueryResultsathena:GetQueryResultsStreamathena:GetTableMetadataathena:GetWorkGroupathena:ListTableMetadataathena:ListDataCatalogsathena:ListDatabasesathena:StartQueryExecutionathena:StopQueryExecutionglue:GetTablesglue:GetTableglue:CancelStatementglue:GetDatabaseglue:GetDatabasesglue:SearchTables
Note that the user or IAM role must also have permission to access the underlying data in S3.
If you would like to write to Athena, make sure to add these permissions as well:
glue:CreateTableglue:UpdateTableglue:DeleteTableglue:CreateDatabase
If you'd like to use the 'tags' functionality, please make sure to include the sts:TagSession permission in addition to the sts:AssumeRole permission.
Updated about 2 months ago